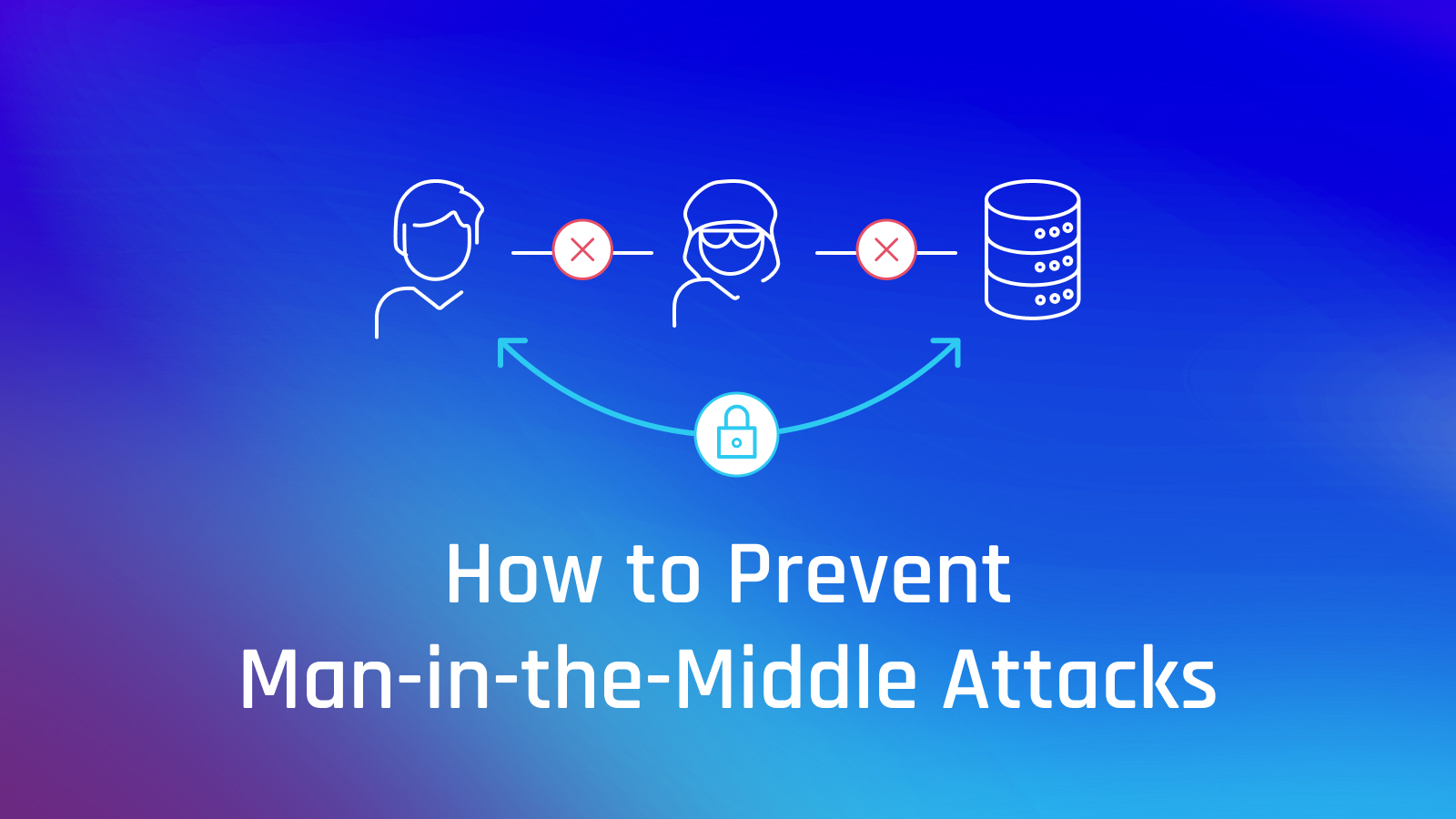
Brilliant Strategies Of Info About How To Avoid Man In The Middle Attack

What protections exist to prevent man in the middle attacks?
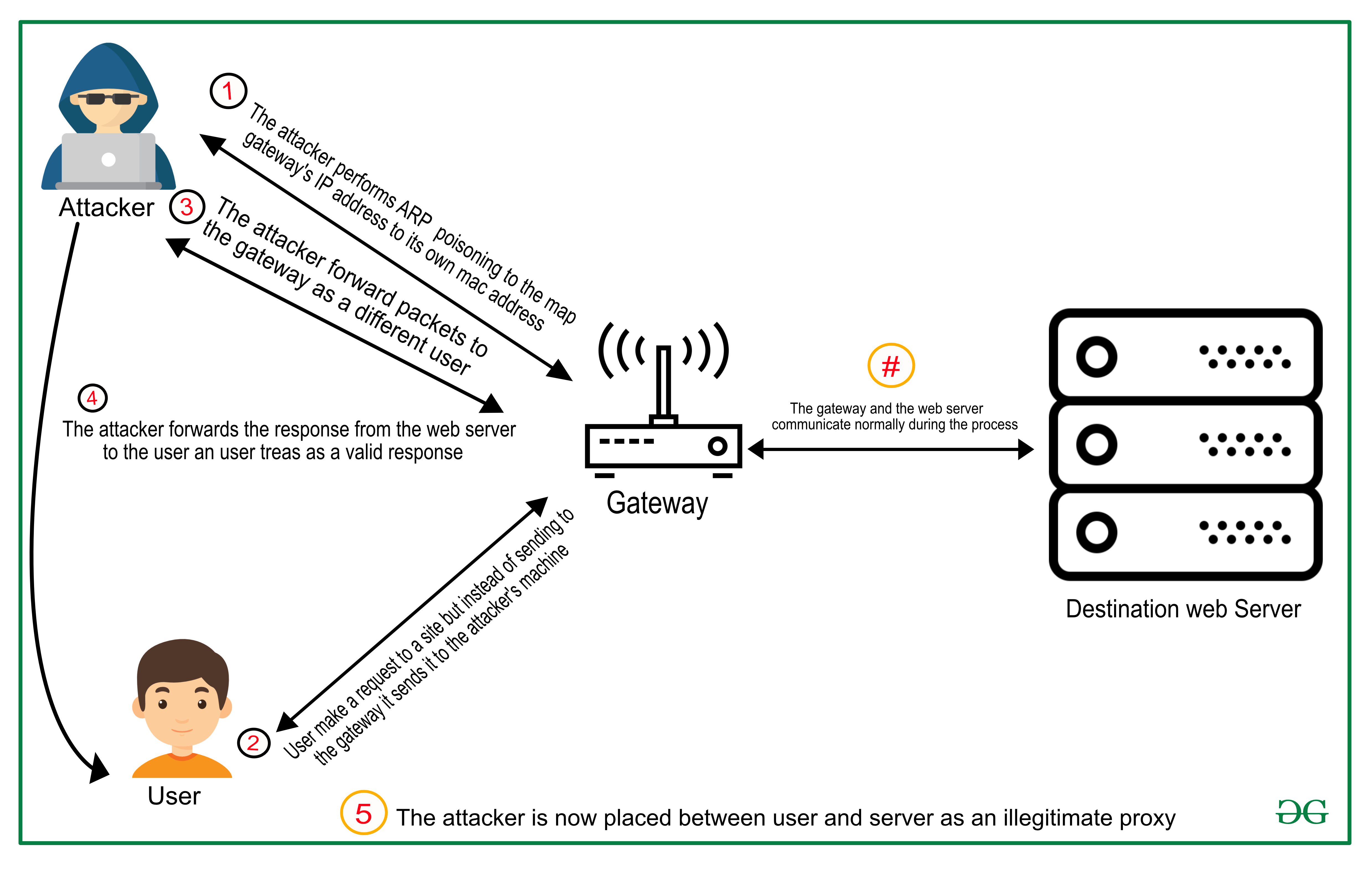
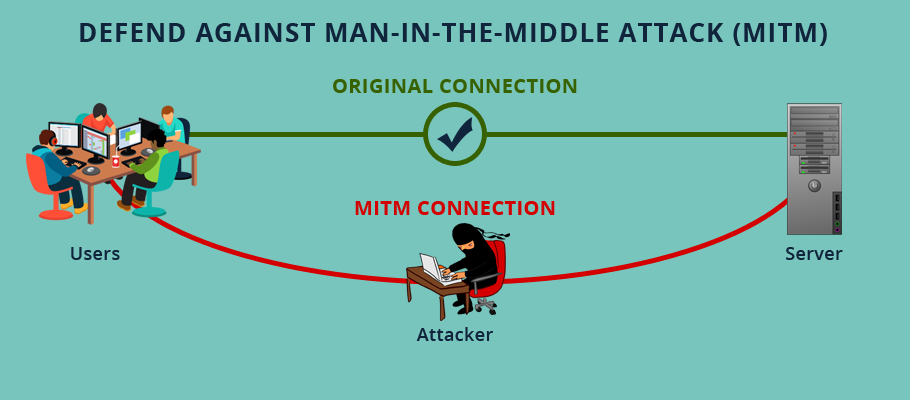
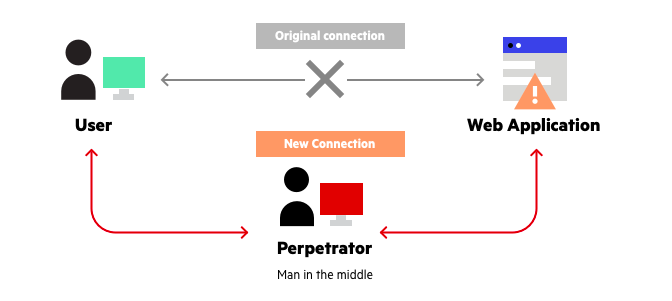
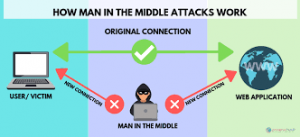
How to avoid man in the middle attack. The truth is, as an individual user,. The technique used by the attacker in this attack is known as address resolution. Avoid connecting to unsecured public wifis when carrying out transactions, online banking, shopping, or other activities that use sensitive information;
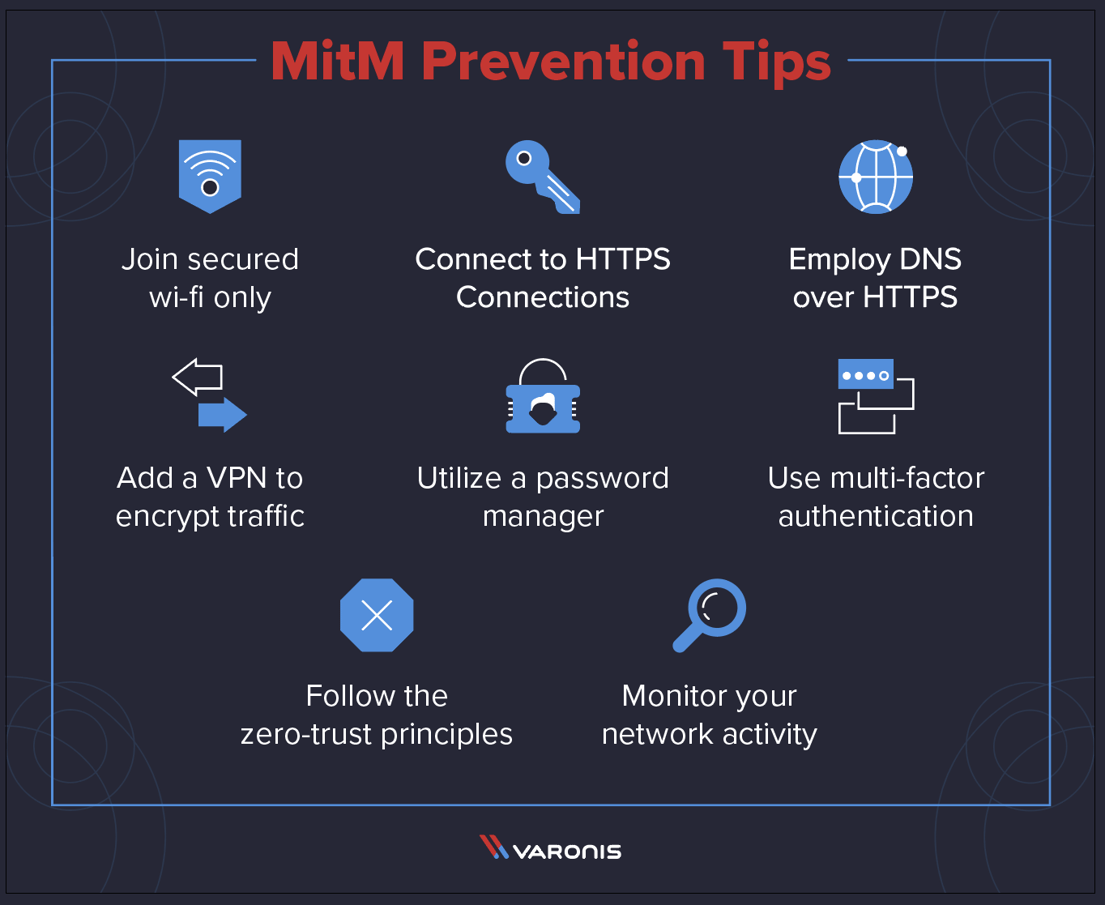
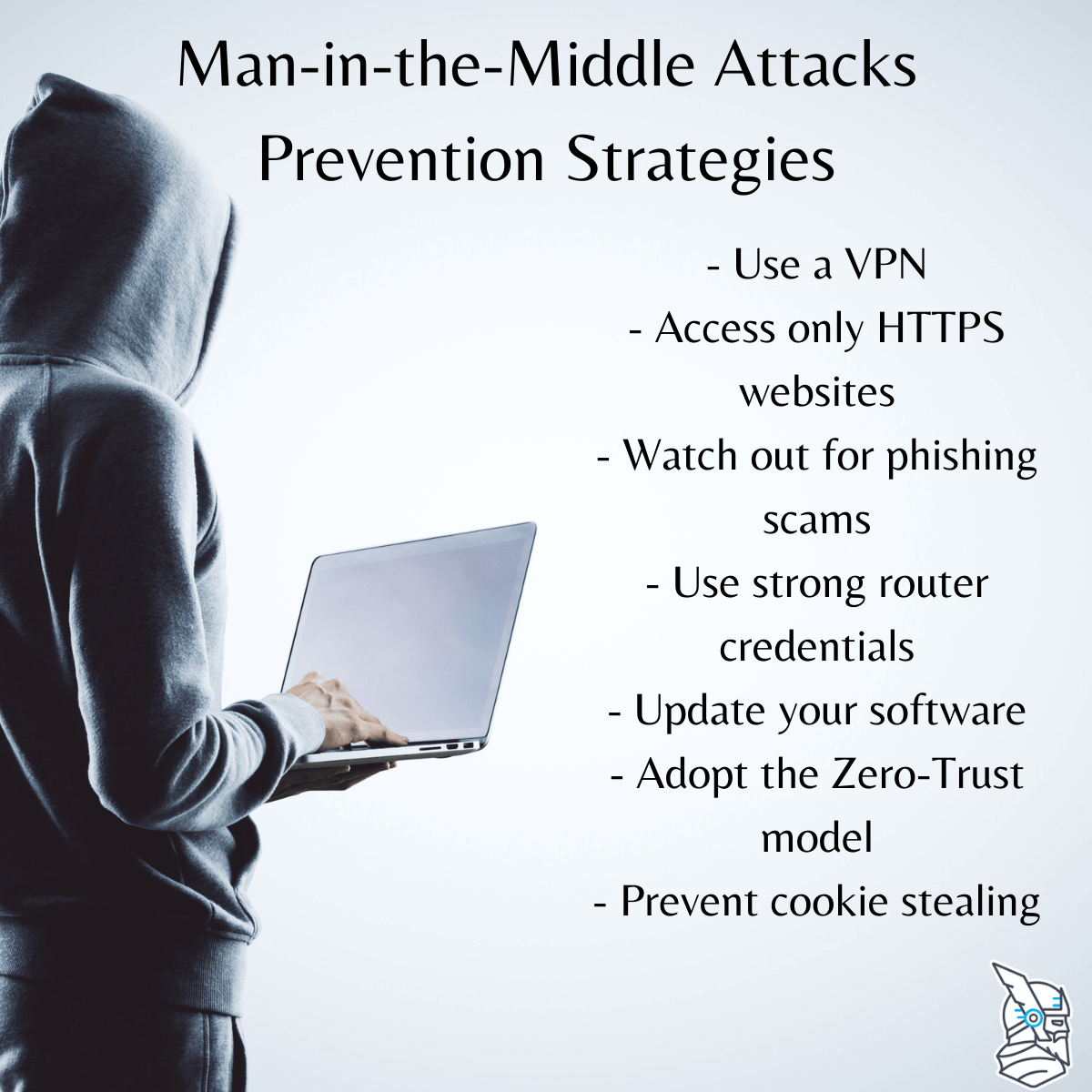
There are some things that can be done to avoid becoming a victim of the mitm and related attacks. Here are several best practices to protect you and your networks from mitm attacks. Use secure dns servers (dns cache):
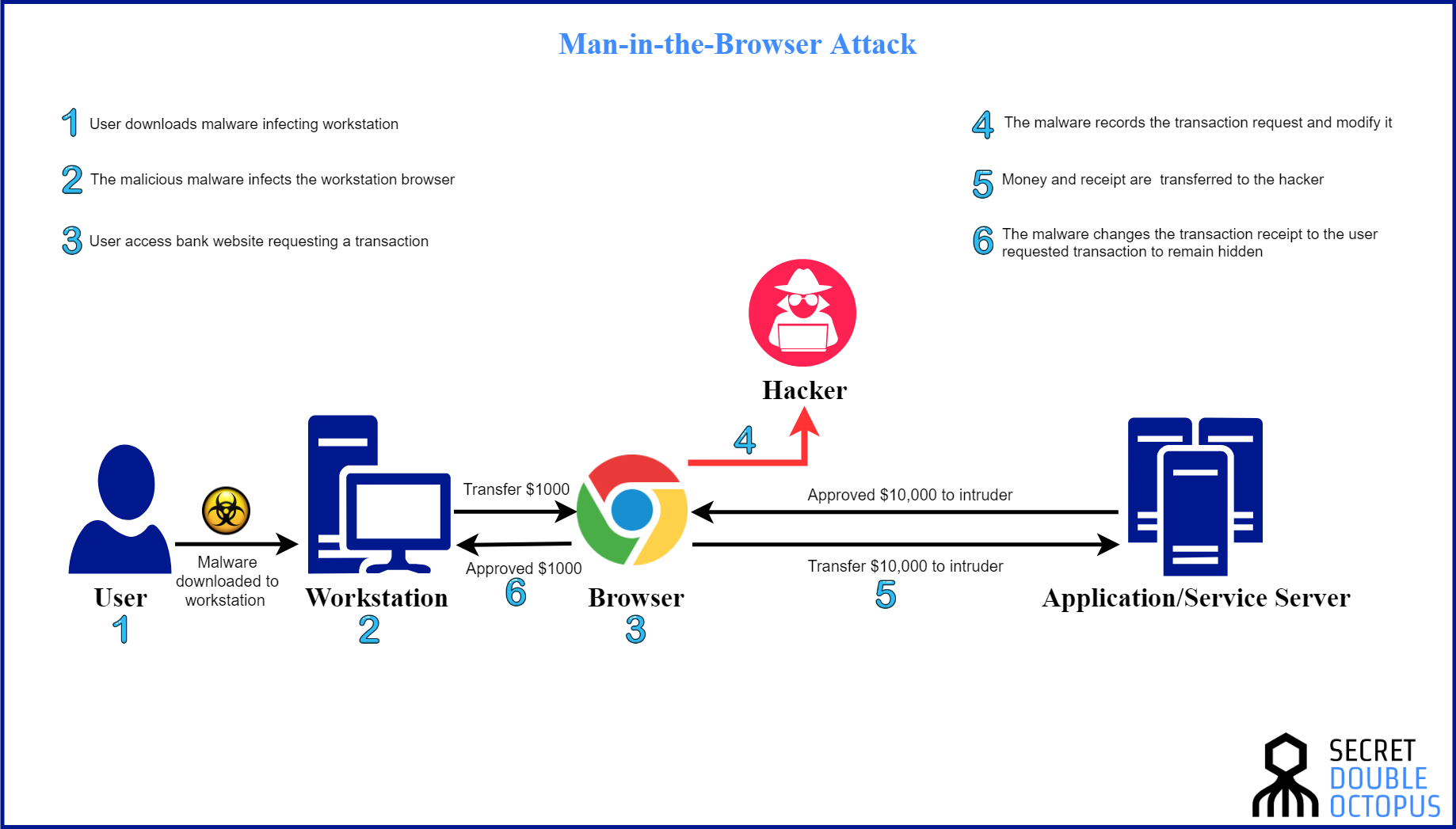
In case yo… see more Despite the endless ways in which these attacks can play out, there are really only a few things that are exploited. A vpn encrypts data, helping stop attacks from.
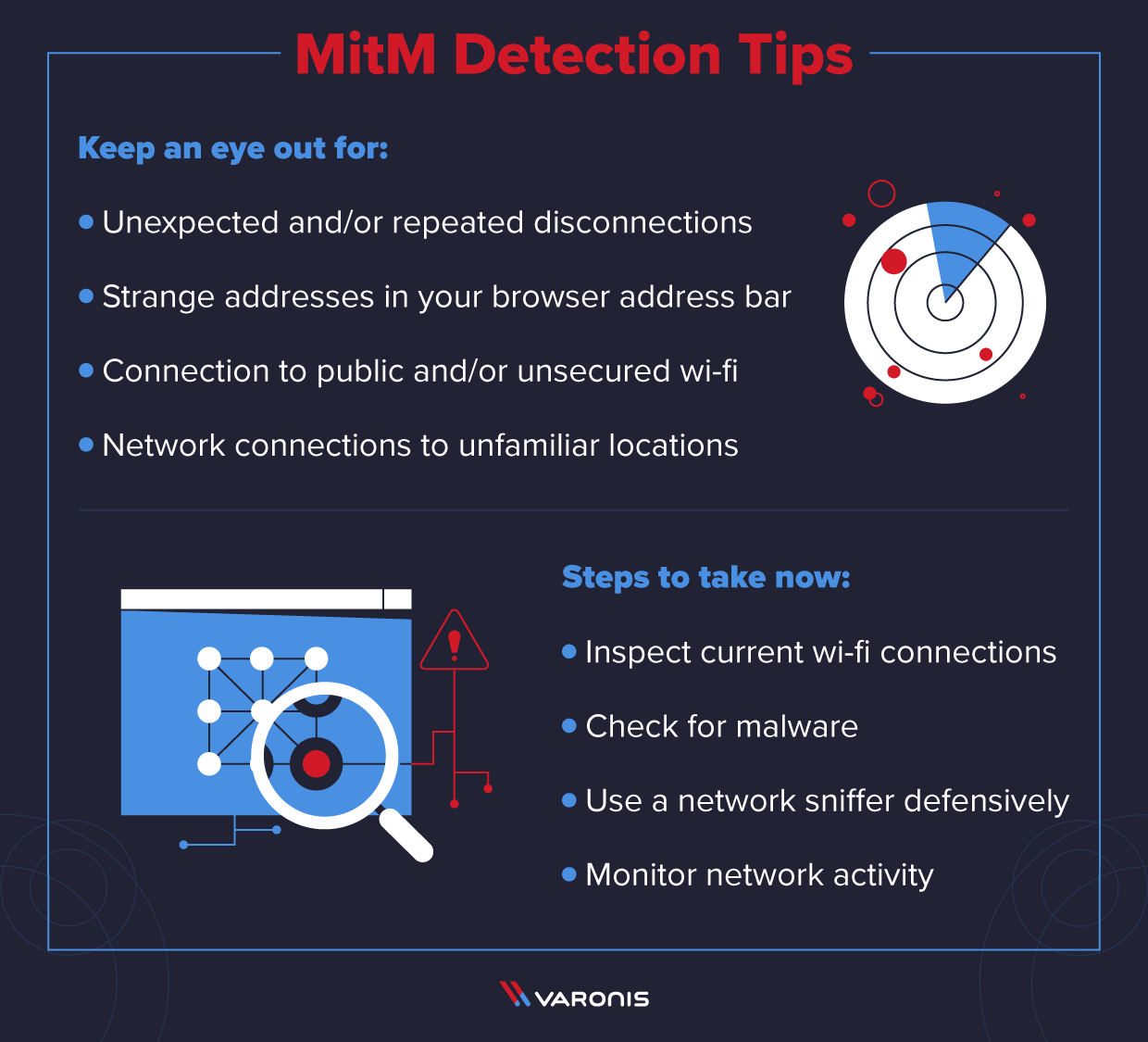
Staying vigilant gives you protection from more frequent attacks. Published apr 22, 2021 by: One of the most dangerous threats in cyber security is the man in the middle attack.
Sound cybersecurity practices will generally help protect individuals and organizations from mitm attacks. In the current business landscape, where mobile. Ensuring that employees know the basic principles of preventing cyber attacks in general, and mitm attack in specific can save a lot of time and money.
Make sure the dns servers. Always use trusted networks and devices to log in to sensitive websites.